TL;DR:
This is an attempt at reverse-engineering the DJI Ronin SC camera gimbal with the following goals:
- using the DJI focus motor separately from the gimbal,
- controlling the gimbal using custom software,
- using the gimbal on a jib/crane-like setup,
- fixing the (many) annoyances and limitations of the official DJI app.
This blog post serves both as my personal notepad and as a starting point for anyone else going down the same path in the future (perhaps with a different DJI device). As the work is still in progress, the post will be updated occasionally.
Part 1: Physical connections
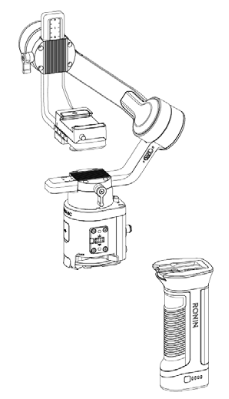
Since this is a rather expensive gadget, I’d like to avoid taking it apart as much as possible. Thankfully, the FCC publishes independent test reports of all RF-emitting gadgets sold in the US, including photos of the wiring and PCBs: https://fccid.io/2ANDR-R181902. Since many of the same accessories fit the Ronin S as well, its FCC report is also quite useful: https://fccid.io/2ANDR-RS11804. If you see photos of components on a blue mat in this article, I’ve likely clipped them from these.
Battery grip mount
The gimbal is split into two main parts – the battery grip and the gimbal head+control unit. Connecting the two is a set of 6 flat contacts on the grip with corresponding pogo pins on the head unit. Presumably, these carry only power, but I have not bothered confirming this.

Side connectors
The gimbal has two sets of side accessory connectors, this time with 8 flat pads on the head and corresponding pogo pins on the accessories. Detaching them from the body by removing the 4 hex screws holding them in place reveals a conveniently labeled PCB and rather annoyingly tiny internal header.
A few minutes of poking with the smallest multimeter probe I could find reveals the following correspondence:
//TODO: include pinout